Products
CYQER unifies historically separate functions into a single agent and platform architecture. Protection is provided for public clouds, private clouds, and on-premise data centers.

The All in one SOC Product by Threatsys Technologies Private Limited
CYQER unifies historically separate functions into a single agent and platform architecture. Protection is provided for public clouds, private clouds, and on-premise data centers.
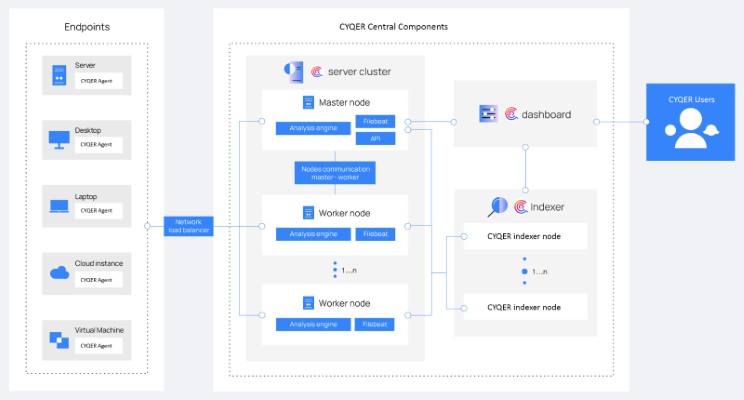
Central Components
The CYQER indexer is a fully scalable engine for analysis and full-text search, tasked with indexing and storing the alerts created by the CYQER server. It can be installed as a single-node or multi-node cluster, any end points, systems based on the specific requirements of the client's environment.
The agents are managed by the CYQER server, which can update and configure them remotely as required. The data received from the agents is evaluated by this component, which utilizes decoders and rules to process it and analyze it for any indicators of compromise by incorporating threat intelligence.
CYQER offers an adaptable and user-friendly web interface that provides a plethora of tools for data mining, analysis, and visualization. The dashboard is a centralized location where CYQER configuration can be managed and the system's status can be monitored.
The CYQER agent is a multi-platform component that runs on the endpoints to be monitored. It provides prevention, detection, and response capabilities in Windows,Linux, Oracle Solaris, Mac os, AIX etc.
CYQER can be deployed in Windows, Linux, Unix, JSON CSV TXT, Commercial Apps, Custom Apps, Change Mgmt, Switches, Firewall, DNS, Routers, DBMS, Storage Mgmt, Cloud, Kubernetes, Puppet, Ansible, Docker.
CYQER Provides analysts real time correlation and context. Active responses are granular, encompassing or-device remediation so endpoints are kept clearn and operational.
The CYQER Security Information and Event Management ( SIEM ) Solutions provides monitoring, detection and alerting of security events and incidents.
CYQER has created an entirely new cloud-based architecture to reduce complexity and improve security while providing stronger endpoint protection.
CYQER is helping organizations detect intrusions, threats and behavioral anomalies. As cyber threats are becoming more sophisticated, real-time monitoring and security analysis are needed for fast threat detection and remediation. That is why our light-weight agent provides the necessary monitoring and response capabilities, while our server component provides the security intelligence and performs data analysis. Read More

CYQER agents can detect hidden files, cloaked processes or unregistered network listers, as well as inconsistencies in system call responses. In addition to agent capabilities, the server component uses a signature based approach to intrusion detection, using its regular expression engine to analyze collecting log data and look for indicators of compromise. Read More
The CYQER rules help make you aware of application or system error, misconfiguration, attempted and/or successful malicious activities, policy violations and a variety of other security and operational issues.
Read More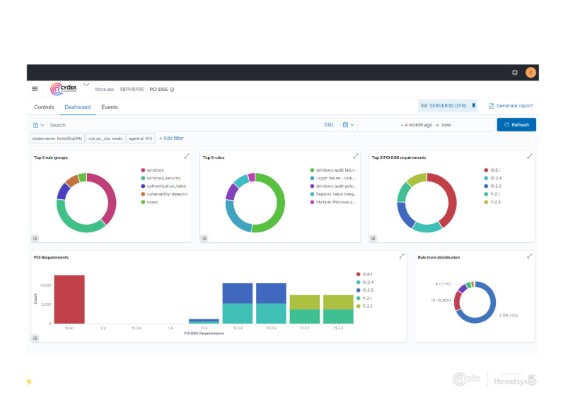

The CYQER rules help make you aware of application or system error, misconfiguration, attempted and/or successful malicious activities, policy violations and a variety of other security and operational issues.
Read MoreCYQER natively identifies users and applications used to create or modify files. File Integrity monitoring capabilities can be used in combination with threat intelligence to identify threats or compromised hosts. In addtion several regulatory compliance standards, such as PCI DSS reuire it. Read More


Where it is correlated with continously updated CVE ( Common Vulnerabiliities and Exposure ) databases, in order to identify well-know vulnerable software. Automated vulnerability assessment helps you find the weak spots in your critical assets and take corrective action before attackers exploit them to sabotage your business or steal confidential data. Read More
CYQER Agents perform periodic scans to detect applications that are known to be vulnerable, unpatched, or insecurely configured. Addionally, configuration checks can be customized, tailoring them to properly align with your organisation. Alerts include recommendations for better configuration, references and mappig with regulatory compliance. Read More

CYQER Provides out of the box active responses to perform various countermeasures to address active threats, such as blocking access to a system from the threat source when certain criteria are met.
CYQER is widely used by PCI processing companies and CYQER UI provides reports and dashboards that can help with Regulatory Compliance such as GDPR, NIST 800-53, GPG13, TSC SOC2, HIPAA and PCI DSS Compliance.
CYQER helps monitoring cloud infrastrcture at an API level, using integration modules that are able to pull security daa from well known cloud providers such as AWS, Azure or Google Cloud. CYQER ligh-weight and multi-platform agents are commonly used to monitor cloud enviornments at the instance level.
CYQER provides security visibility into your Docker hosts and containers, monitoring their behavior and detecting threats, vulnerabilities and anomalies. Agent has native integration with the Docker engine allowing users to monitor images, volumes, network settings and running containers.
Businesses rely on their IT infrastructures to support nearly every aspect of their operations. At the same time, security threats ranging from cyberattacks to malicious user activity can put network security and data integrity at risk. For comprehensive protection, businesses are turning to CYQER all in one Security and Information Event Management (SIEM) tools, software programs to help monitor log activity—and flag suspicious incidents—throughout an IT environment.
Learn MoreFully protected data, regular application of security patches and hardening practices. Compliant with PCI DSS and SOC2. A ready to use solution, with no additional hardware or software required, driving down the cost and complexity.
Around-the-clock SOC services – securing any environment, any application. Our Security Operation Center (SOC) services are available to help protect all of your environments, even those not currently managed by Threatsys Technologies — such as your on-premises data center, branch locations, colocations.
SOC-as-a-Service goes beyond what traditional Managed Security Service Providers (MSSPs) and Managed Detection and Response providers offer. Traditional MSSPs can offer advanced Security Operations Center (SOC) capabilities for threat detection and response.



Every organization has a multitude of network devices that work together to facilitate everyday business operations. For an attacker, all it takes is one security loophole in any of these endpoints to bring business operations to a halt. With so many devices operating simultaneously, it is difficult to figure out exactly where you are vulnerable. These devices do generate security data for every event, but the sheer volume of data makes it difficult to focus on the key indicators of an attack. A SIEM solution protects your enterprise network from cyberattacks and insider threats. It collects and analyzes the security data generated by your devices in real time, alerting you in time about vulnerabilities, indicators of compromise, or any suspicious activity.
Detect internal threats, such as data exfiltration and user account compromise, by recognizing subtle changes in user activity. Monitor all active VPN connections, and receive alerts on unusual VPN activities, VPN access from malicious sources, and more. Audit critical changes in your Active Directory infrastructure and Azure AD in real time. Track all critical events in your public cloud infrastructure, including AWS, Microsoft Azure, Google Cloud Platform, and Salesforce. Identify suspicious or blocklisted IPs, URLs, and domains intruding into your network by correlating your log data with reputed threat feeds. Discover and classify sensitive files, audit users' file activities, and analyze file permissions to enable content- and context-aware data protection. Automate your response to events with easily configurable workflows to save critical response time.Detect, disrupt, and prevent sensitive data leaks via endpoints, like USBs and printers, email, web applications, and more with real-time security monitoring. Ensure compliance with regulatory mandates such as the PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA with predefined report templates.
Security Analyst/L1 Engineer: Taking Control of your Log Data and help with on-boarding Alerting and reporting L2 Analyst: Certified and trained ‘Eyes on Screen’ Investigations, analysis and forensics Incident management Proactive actions and help on hand when you need to respond or investigate. L3/SOC Manager Manages the Security Operations Team and reports to the CISO. Supervises the security team & provides technical guidance. Responsible for creating Processes, assessing Incident reports, and Developing and implementing Crisis Communication Plans. Incident Response (IR) Consultants: Escalation and in-depth investigations with advanced IR tools Malware reverse engineering, host based analysis, network packet inspections, deep dive investigations On and off-site forensic capabilities Chief Information Security Officer: Responsible for defining and outlining the organization’s security operations Provide the final word on strategy, policies, and procedures. Responsible for managing overall compliance
“Without a partner like Threatsys, we would have spent years trying to build infrastructure to support our goal. Now, we have the technological backbone CYQER that will enable us to achieve our global ambitions and know that we have a trusted partner that will continue to support us on that journey."

“Transparency is an overall net win consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quiqa Ut e nostrud exercitation ullaco laboris nisi ut aliquip”

“Transparency is an overall net win consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quiqa Ut e nostrud exercitation ullaco laboris nisi ut aliquip”

You can get your Free GAP Assessement Report of your Organisation to know your Cyber Security Posture. Know your Cyber Score and accordingly go for the SOC Solutions.